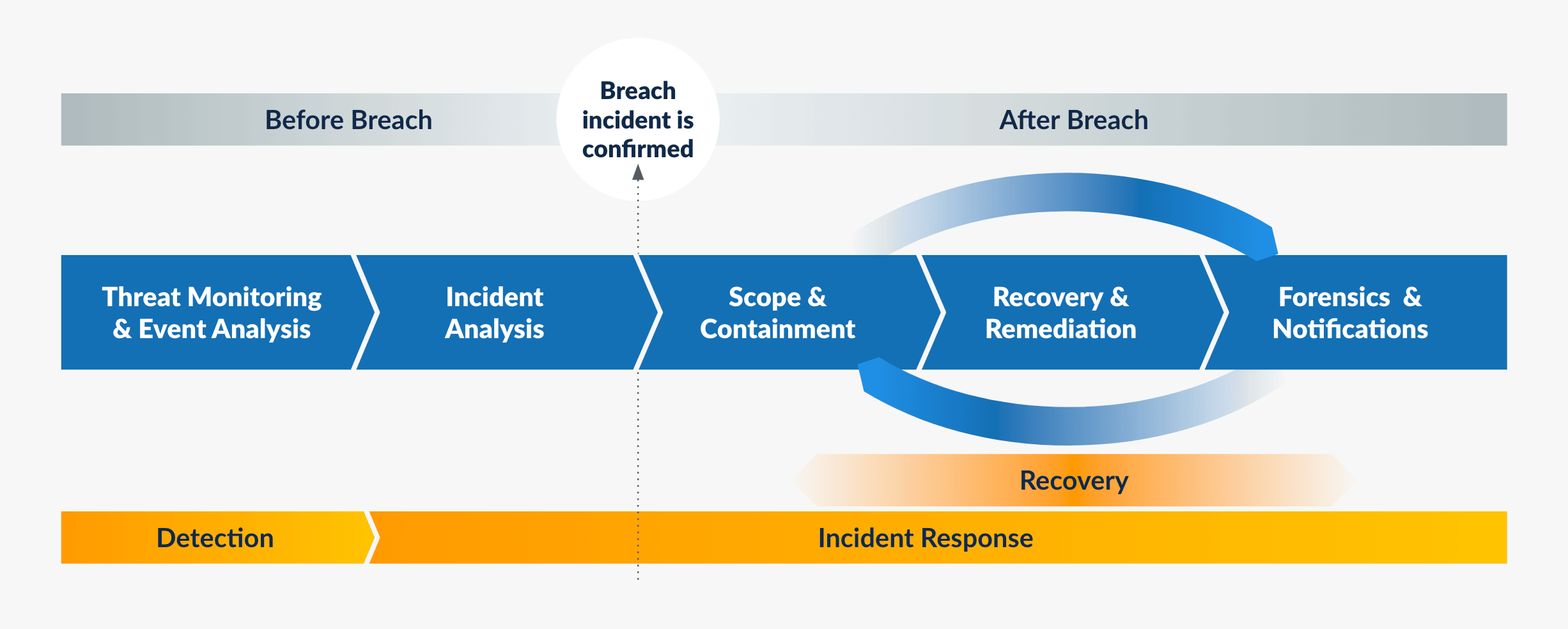
IR and remediation efforts fall under two broad categories:
“Peacetime Activities” — Hunting for Undetected Threats
Mature, at-scale security teams have “peacetime” programs around threat hunting. This is typically to “hunt” for undetected threats that might have penetrated cyber defenses and have a presence in the enterprise. Finding and confirming threats as part of these threat hunts initiate the incident response process to drive the attacker out, contain the incident, and then initiate remediation and recovery operations.
“Wartime Activities” — Following an Incident, Determining Scope, Impact, and Timeline
During the course of regular security operations, if incidents are confirmed, the team will determine the initial intrusion vector, timeline, and scope of infection during the investigation and response. These are dependencies for subsequent actions around containment, remediation, and recovery.
Gaps in the Process
For both peace and wartime actions, security and IR teams typically use primary security tools like SIEM and EDR to search for indicators of compromise (IoCs) and indicators of attack (IoAs). These could include static file attributes (filenames, file hashes, etc.) and behavioral attributes (process, name, etc.). However, security teams might not have all the data available or might need additional information to assess the situation properly.
Fortunately, backups contain this data across an extended timeline and your enterprise fleet (edge, data center, public cloud, and SaaS apps). What if enterprises could access this rich historical archive for more than just recovery, utilize it to search for threats, and take action?
Filling the Gaps in Response — Threat Hunting with Druva
That’s where Druva comes in — we take a comprehensive approach that allows customers to search and take action on threats in their backed-up data. Let’s look at where the security team can investigate threats as part of a wartime or peacetime scenario in their end-user data distributed across edge devices (Win/Mac) or SaaS collaboration apps (Microsoft 365/Google Workspace).
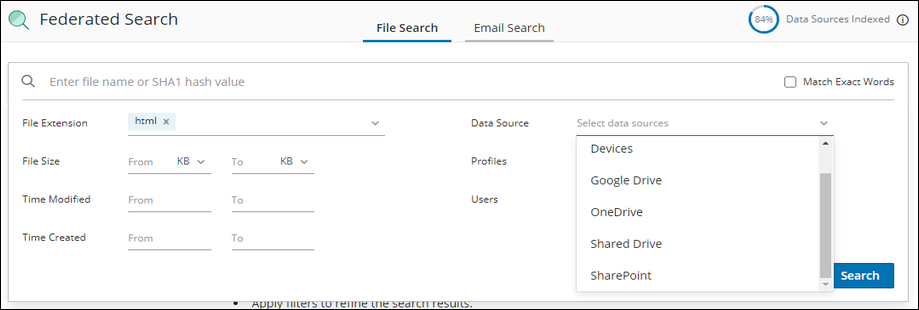
1. Search
Your security team can search for specific static file IoCs. Backups can complement security tools to allow the customer to determine the infection, scope, and timeline, and help initiate the next steps of containment, cleanup, and recovery. Druva’s Federated Search is a powerful tool that leverages metadata of backups. This Federated Search capability is critical to enabling the location of sensitive or malicious data that is backed up by users and offers unique insights that go beyond the raw data itself. Admins can search for data based on the following criteria:
Search based on this metadata provides matching results across historical backups. These offer an indication of which snapshots contain potential infections and the overall timeline of the attack. Admins can take subsequent containment, remediation, and recovery actions based on this information.