Data security is the practice of protecting data from unauthorized access, use, disclosure, disruption, modification, or destruction. It's a critical aspect of modern computing, especially in an age where data breaches are becoming increasingly common. According to IBM’s Cost of a Data Breach report, which analyzed 604 affected organizations from February 2023 to March 2024, the global average total cost of a data breach rose by 10% compared to the previous year, reaching USD 4.88 million across all industries. Malicious insider attacks proved to be the most costly, averaging USD 4.99 million. The healthcare industry had the highest average breach cost, approximately USD 9 million, followed by the Financial Industry with an average cost of around USD 6 million.
Insider Threats
A major security risk often underestimated is the threat posed by insiders. These individuals, including current or past employees and business associates, have access to critical confidential information and the potential to harm your company, either deliberately or inadvertently. A Cybersecurity Insiders 2024 report reveals a sharp rise in insider threats, with 76% of organizations experiencing these incidents in 2024 compared to 66% in 2019. The 2024 Data Breach Investigations Report (DBIR) highlights key trends in cybersecurity threats and breach patterns. Among the findings, ransomware and social engineering incidents have increased significantly, with human involvement contributing to 68% of breaches, often through social engineering or accidental errors. Healthcare faces particularly elevated risks from insider threats, frequently linked to the misuse of sensitive data. Additionally, phishing attacks have become more frequent and advanced, with the average time for users to fall victim now under 60 seconds. The findings underscore the need for robust security measures, including employee training, to combat these evolving threats.
The Microsoft Security Response Center outlines the Ten Immutable Laws of Security to provide guidance around how to enhance data security. They are:
If a ‘bad actor’ can persuade you to run their program on your computer, it's not solely your computer anymore.
If a ‘bad actor’ can alter the operating system on your computer, it's not your computer anymore.
If a ‘bad actor’ has unrestricted physical access to your computer, it's not your computer anymore.
If you allow a bad actor to run active content on your website, it's not your website anymore.
Weak passwords trump strong security.
A computer is only as secure as the administrator is trustworthy.
Encrypted data is only as secure as its decryption key.
An out-of-date anti-malware scanner is only marginally better than no scanner at all.
Absolute anonymity isn't practically achievable, either online or offline.
Technology isn't a panacea.
These ‘bad actors’ can refer to both external (hackers) and internal threats (rogue administrators or malicious insiders). Both groups pose significant cybersecurity risks, particularly when they gain elevated privileges. With such access, they can steal, modify, encrypt, or delete sensitive data. These actions are usually motivated by financial gain or, in the case of disgruntled employees, to cause disruption to business continuity.
Backups are often regarded as the final safeguard against data loss, playing a crucial role in helping organizations recover from incidents. This makes them prime targets for both hackers and rogue administrators. While external hackers often encounter substantial obstacles when attempting to bypass an organization’s full security infrastructure. However, rogue administrators with privileged access can more easily exploit vulnerabilities. They have the ability to delete backups or transfer them to external environments, jeopardizing the organization’s capacity to recover lost or compromised data. Additionally, they can alter backup retention policies, allowing for the deletion of backups or disruption of compliance.
So how can we prevent rogue admins from deleting backups? Several strategies can be implemented.
Implement least-privilege access: Ensure that admins only have the access they need to complete their specific tasks, minimizing unnecessary permissions.
Revoke or restrict access: If a rogue admin is suspected, immediately revoke their access or reduce it to "view-only" for all admins until the issue is resolved.
Monitor and log admin activities: Ensure all actions by admins are logged, with alerts for suspicious behavior and regular reports for monitoring.
Apply immutability: For highly sensitive data, immutability can be enforced to prevent modifications or deletions.
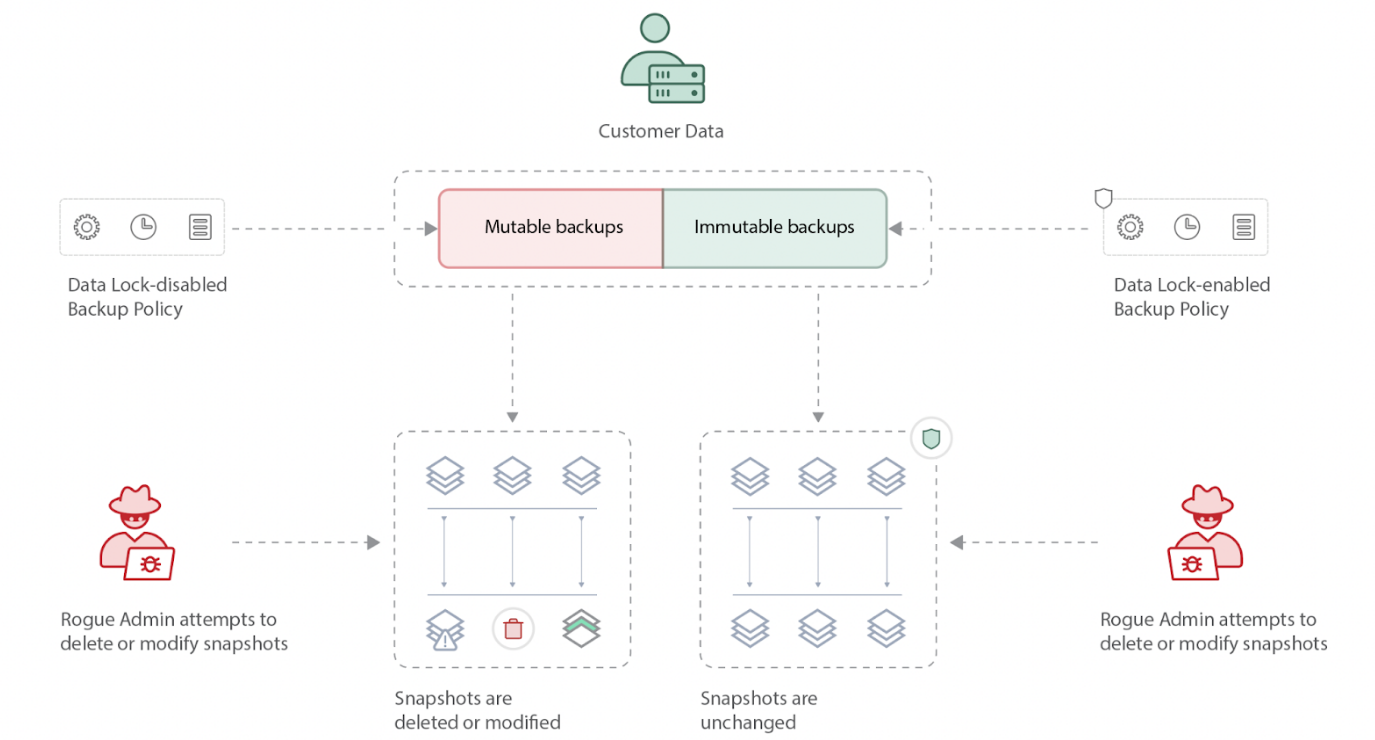
What is immutability? Immutability refers to data that, once created, cannot be changed or modified. This ensures that the original data remains intact, providing a critical layer of protection against tampering and corruption.
How does Druva Protect Against Insider Threats?
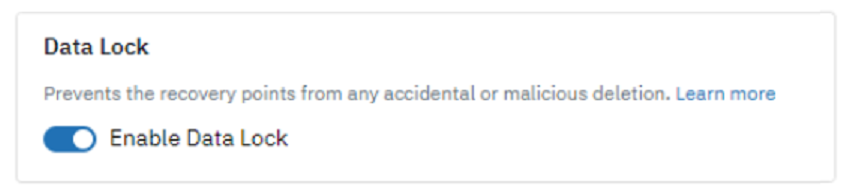
Foundationally, Druva provides immutable backups that cannot be tampered or modified by anyone. Moreover, Druva offers a feature called Data Lock, which, when enabled, ensures that backed-up data cannot be modified, tampered with, encrypted, or deleted by anyone, including rogue admins or hackers, until its specified retention period expires. Even if credentials are compromised, Data Lock prevents deletion or alteration of the backup data. Data Lock does allow ‘Bad actors’ to change retention or modify backup policies.
Data Lock solves governance problems - it can be unlocked, upon validated request, by Druva support (to delete non-compliant data). Data Lock is available for all workloads in Druva.