In cryptography, the Federal Information Processing Standard (FIPS) is a standard that defines the security requirements for cryptography algorithms and the software that implements them. It is used by the U.S. federal government and other organizations to ensure that cryptographic systems and solutions are secure and reliable. The BoringSSL library in Go provides support for the FIPS mode. However, the use of the BoringSSL FIPS mode also incurs some overhead compared to when it is not used. In this blog, we will explore the overhead caused by BoringSSL FIPS mode in Go, as well as the impact on overall performance.
How Tests are Performed
We selected the AES-GCM encryption algorithm for our benchmarking. AES (Advanced Encryption Standard) is a FIPS-compliant symmetric encryption algorithm. Symmetric algorithms use the same key for both encryption and decryption. AES can use key lengths of 128, 192, and 256 bits. AES along with Galois/Counter Mode (AES-GCM) provides both confidentiality and authentication. We need to provide a Nonce as input to AES-GCM. Nonce (a number used only once) is a non-repeating sequence that AES-GCM uses internally to generate different keystreams for different messages even if encrypted with that key.
Parameters
We used AES-GCM encryption algorithm and varied the below parameters:
Key size: 128 bits, 256 bits
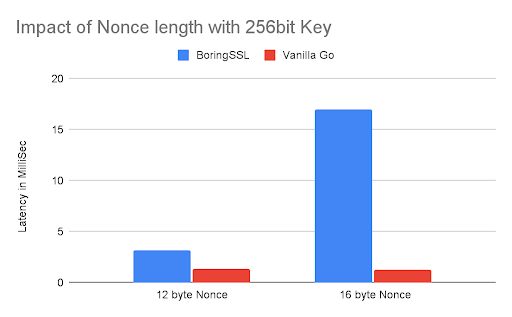
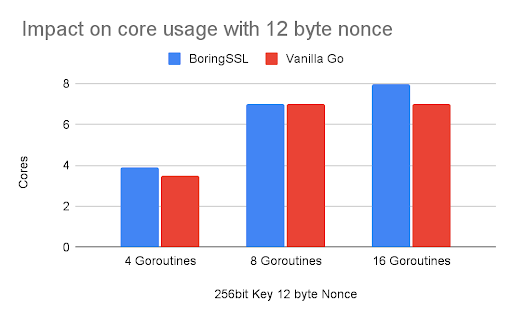
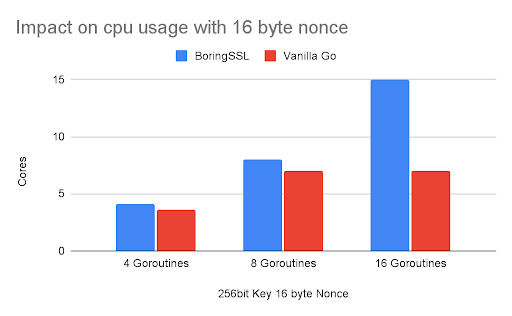
Nonce size: 12 bytes, 16 bytes
Number of Goroutines running in parallel to perform encryption: 4, 8, 16
Data block size: 1MB
CPU usage and time required to complete one encryption operation are measured.
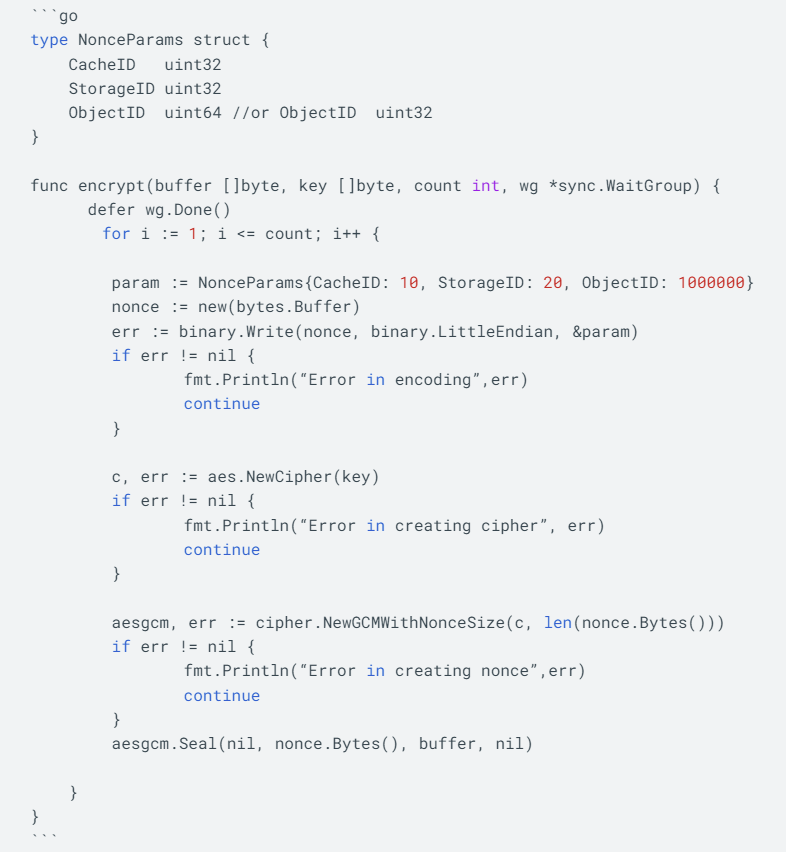
Code
We used the below code snippet for the test runs. We ran this test in multiple goroutines as per test configuration with the required changes in Nonce length.