In part one of this five-part series, we discussed how we can achieve data archiving in Amazon S3. To follow up, we will discuss how to achieve data confidentiality. We will walk you through some AWS features like S3 data encryption, access analyzer, Amazon Macie, and Amazon CloudTrail data events for Amazon S3 as a data source for Amazon GuardDuty. Please note that these features may or may not be used together based on your organization’s needs.
Encrypting Amazon S3 Data
Amazon S3 data can be protected while in transit (i.e., to and from Amazon S3) and at rest (i.e., at storage disks in Amazon data centers). Data in transit is secured using Secure Socket Layer/Transport Layer Security (SSL/TLS) or client-side encryption. Amazon S3 allows both HTTP and HTTPS requests. You can enforce HTTPS requests and enforce object encryption using specific KMS keys and Amazon S3 bucket policy, which we will discuss in part five of the series.
For protecting data at rest there are two parts:
- Server-side encryption
- Client-side encryption
Server-side encryption allows Amazon S3 to encrypt your object before saving it on disks in the data center and then decrypt it when you download the objects. You have three options for this:
- Server-side encryption with Amazon S3-managed keys (SSE-S3)
- Server-side encryption with KMS keys stored in Amazon Key Management Service (SSE-KMS)
- Server-side encryption with customer-provided keys (SSE-C)
You should consider using the Amazon S3 default keys (KMS console: aws/s3) if you’re uploading or accessing objects using AWS Identity and Access Management (IAM) principals in the same account as the KMS key, and/or if you don’t want to manage policies for the KMS key. However, if you have specific compliance or security requirements, you should consider using a customer-managed key that will allow you to create, rotate, disable, or define access controls for the key and grant cross-account access to your objects. This is because it is possible to configure the policy of a customer-managed key to allow access from another account.
On the other hand, client-side encryption allows you to encrypt data yourself using your own encryption keys and then upload the encrypted data to Amazon S3. You can achieve this in two ways:
- Use a key stored in Amazon Key Management Service (Amazon KMS)
- Use a key that you store within your application
Amazon S3 Access Analyzer
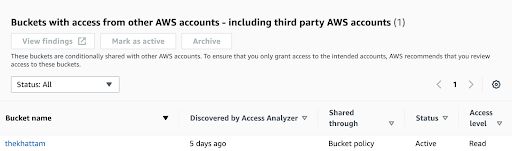
Access Analyzer for Amazon S3 is a free service powered by Amazon IAM that alerts you if Amazon S3 buckets are configured to allow access to anyone on the internet or other AWS accounts, including AWS accounts outside of your organization. Examples include: when an Amazon S3 bucket has read or write access provided through a bucket access control list (ACL), a bucket policy, a multi-region access point policy, or an access point policy. For enabling Access Analyzer for Amazon S3, you would need to create an account-level IAM analyzer for each region from the AWS IAM console.