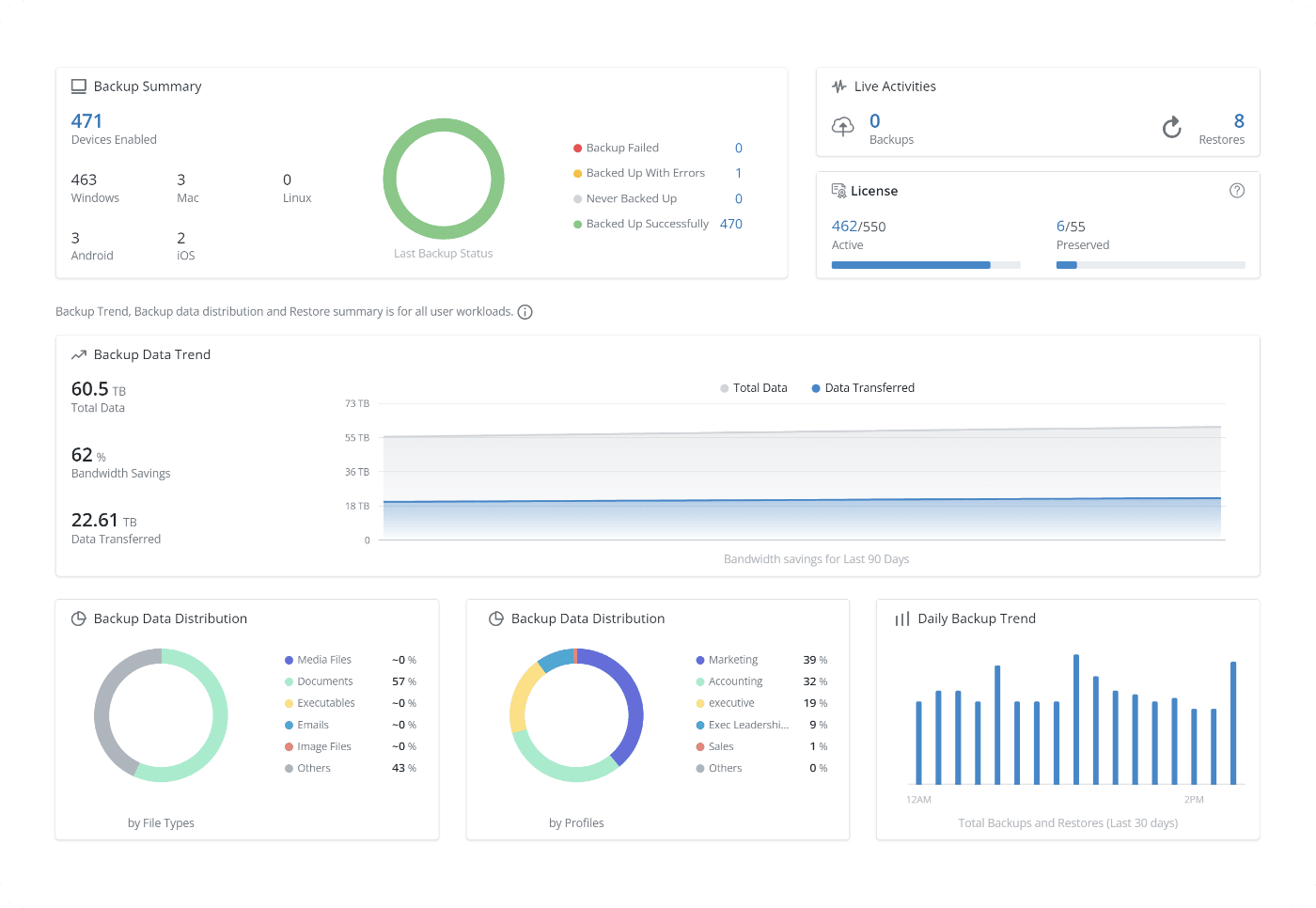
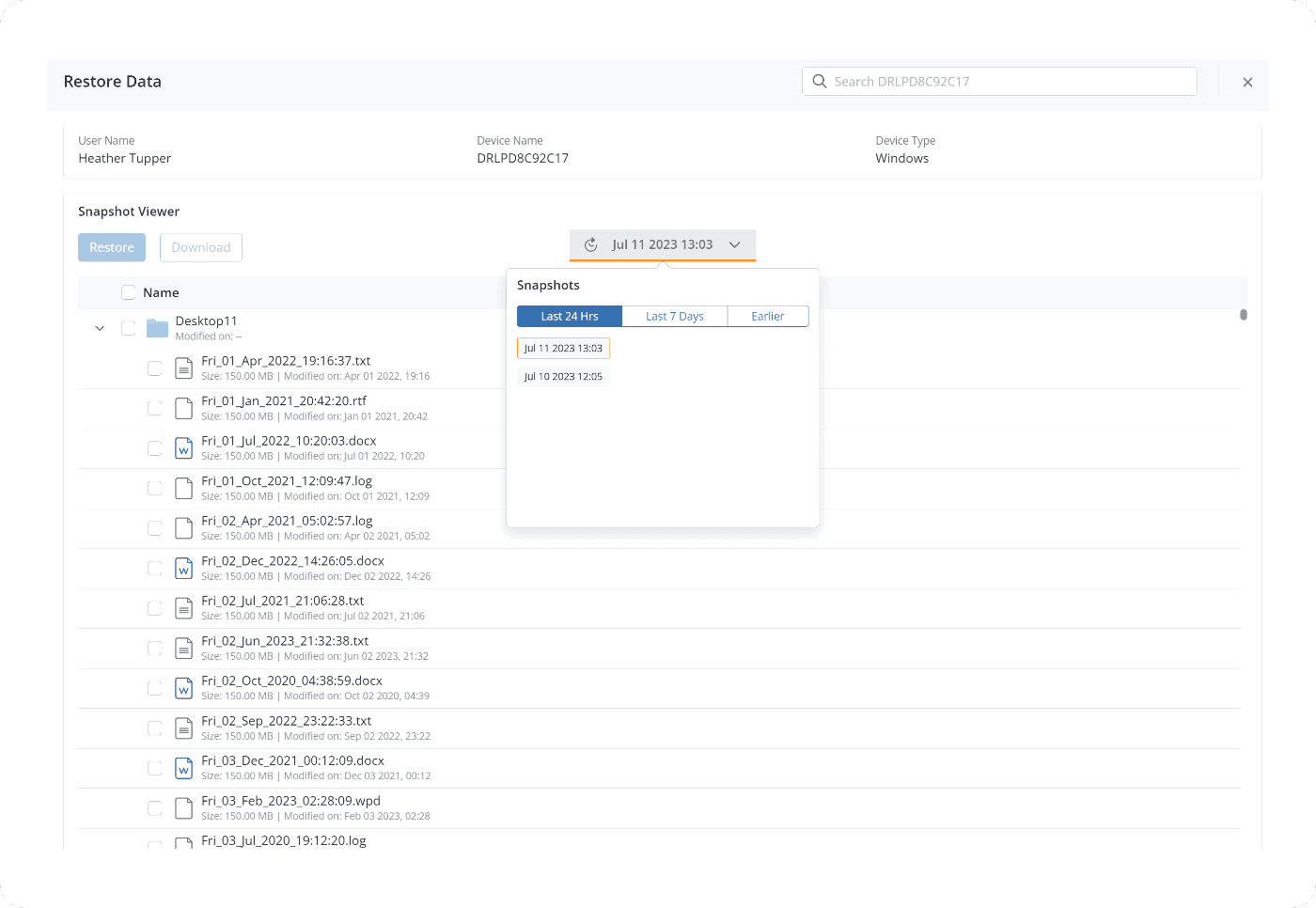
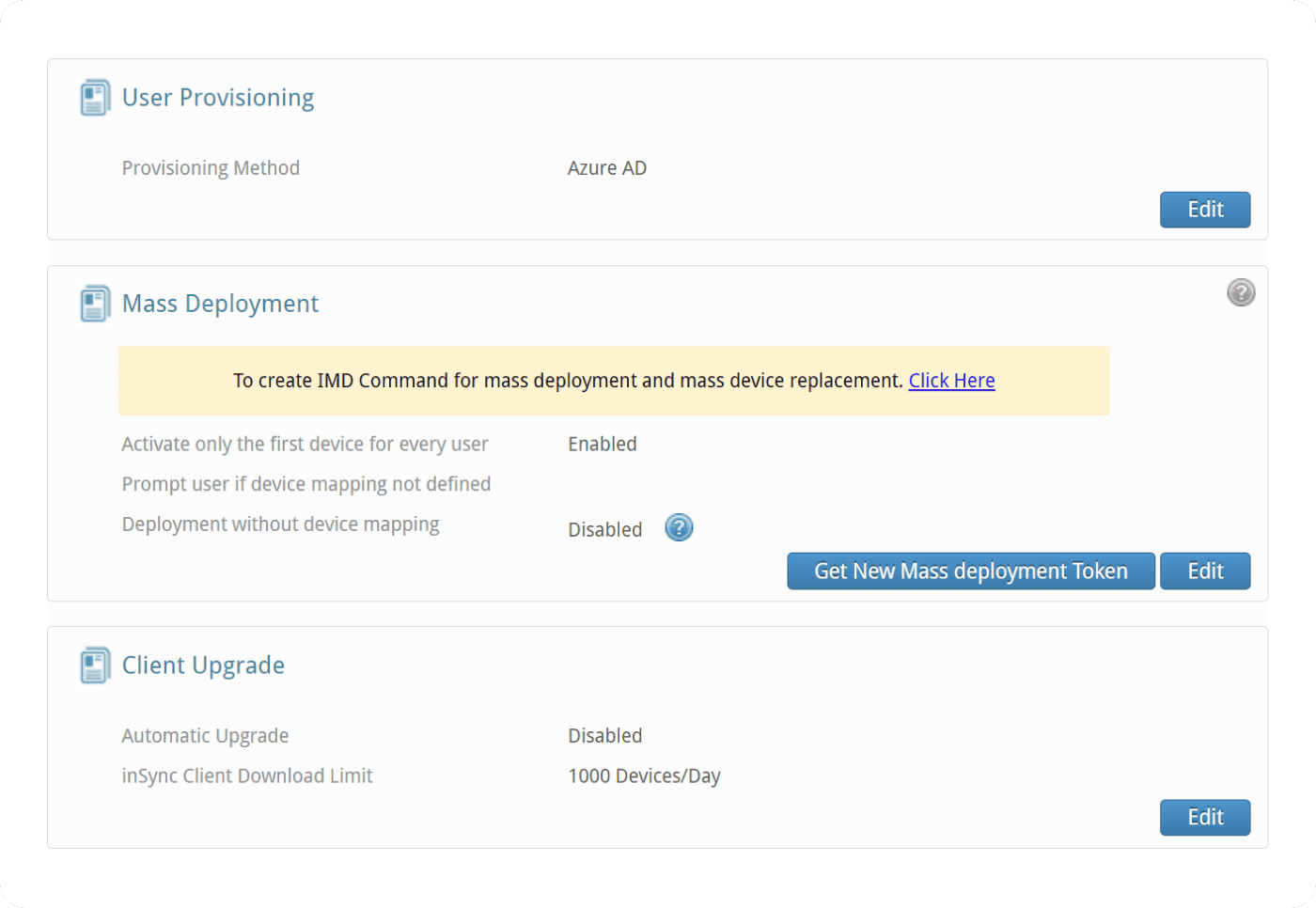
At-a-glance visibility to backup status, user devices, and health monitoring with an admin console that can be accessed from anywhere in the world.
Manage and secure endpoints from one centralized platform
Automate backups across Windows, macOS, and Linux, while managing business-critical data through an intuitive interface. Simplify IT operations and ensure seamless control over digital assets in the cloud.
Improved ransomware response and recovery
Ransomware protection and recovery with air-gapped and isolated data, anomaly detection, flexible recovery options, and point-in-time recovery.
Accelerate legal hold and eDiscovery
Automate the handling of legal hold requests through the preservation and culling of data. Facilitate security investigations with federated metadata search capabilities.
Minimize compliance risks and penalties
Ensure adherence to recent regulations such as GDPR and CCPA. Proactively identify compliance breaches and take action through defensible deletion.
Manage data migration and device refresh with ease
Efficiently migrate user data and settings on devices, minimizing disruptions to business and productivity. Remove third-party dependencies during OS upgrades or device replacement.